Fake Windows BSOD used to push remote-access trojan in hotel-focused campaign
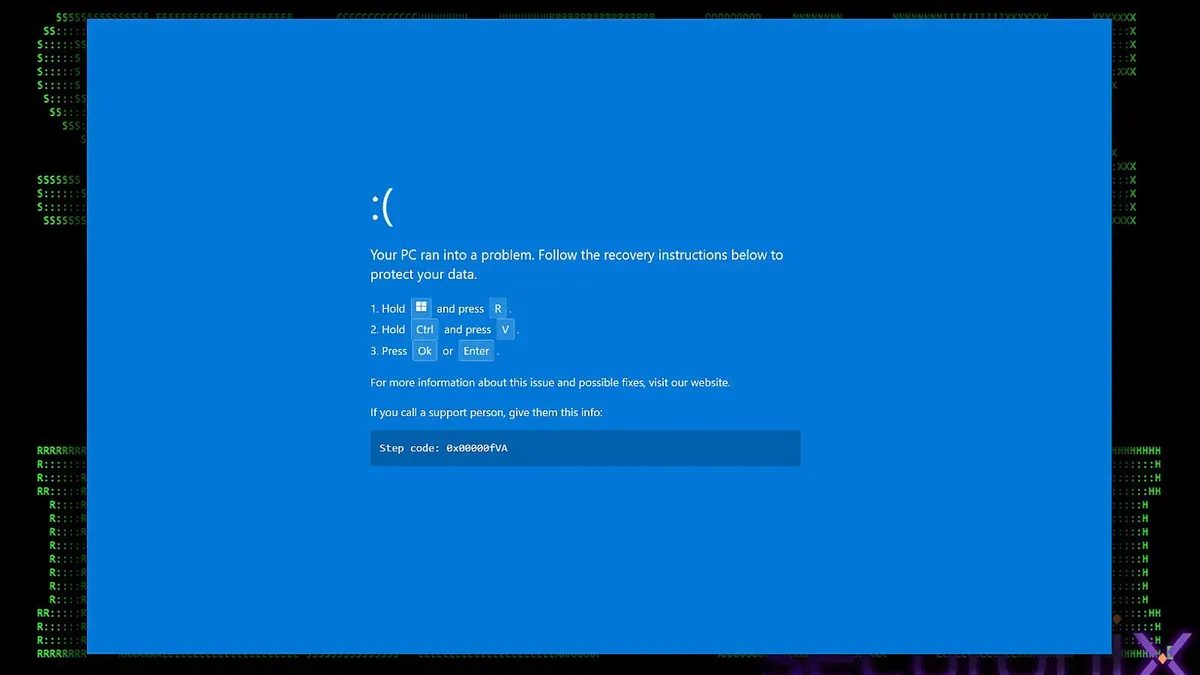
Security firm Securonix says a campaign dubbed PHALT#BLYX uses fake Windows BSOD screens to trick victims into installing a remote access trojan, and that the effort is aimed at the hotel and hospitality industry. According to Securonix, the attack begins with a phishing email linking to a fake Booking.com page.
A fake CAPTCHA on that page then triggers a phony BSOD and prompts the user to copy and paste code. That ClickFix tactic runs a PowerShell command that downloads an MSBuild project file named v.proj, disables Windows Defender, and establishes persistence by creating a URL in the startup folder.
The final payload is an obfuscated version of DCRat, which Securonix says can establish remote access, log keystrokes, run malicious code via legitimate processes, and install secondary payloads. Securonix notes the phishing emails list room charges in euros, suggesting European hotel targets, and that Russian language found in the v.project file links the campaign to Russian attackers; the firm adds the campaign was launched during the busy holiday season and leverages Booking.com's familiarity.
Securonix offers defensive advice for organizations and individuals at risk: educate staff about ClickFix tricks, verify phishing emails claiming to be from hospitality services, monitor MSBuild.exe and other legitimate executables for unusual activity, watch for suspicious .proj and .exe files in ProgramData or startup folders, and enable PowerShell Script Block Logging.
Key Topics
Tech, Phalt#blyx, Dcrat, Booking.com, Securonix, Powershell
