Attackers Abuse Google Cloud Email Feature to Deliver Multi-Stage Phishing
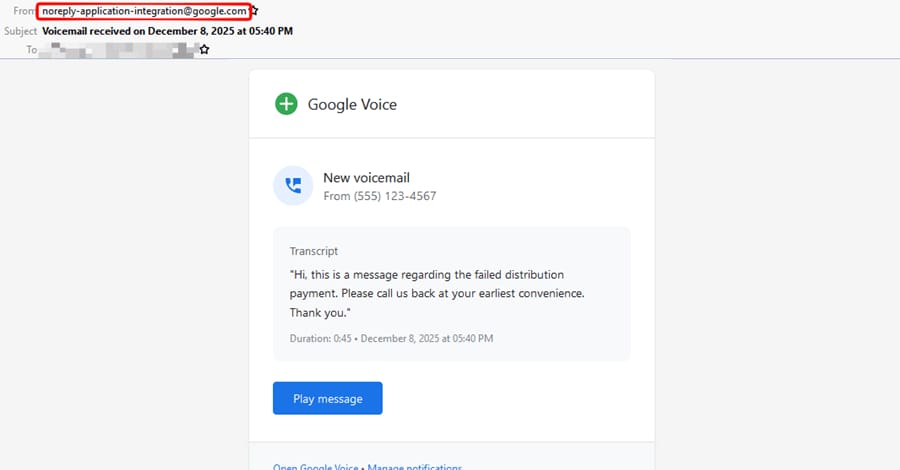
Security researchers disclosed a phishing campaign that abused Google Cloud's Application Integration service to send messages from a legitimate address (noreply-application-integration@google[.]com), allowing attackers to bypass traditional email security filters. The emails imitated routine Google notifications such as voicemail alerts and file-access or permission requests to appear trustworthy.
Check Point reported 9,394 phishing emails sent to roughly 3,200 customers over a 14-day period in December 2025, targeting organizations across the U.S., Asia-Pacific, Europe, Canada and Latin America. At the center of the abuse is the Application Integration "Send Email" task, which can be configured to send notifications to arbitrary addresses (support documentation notes a 30-recipient maximum).
Messages used Google-style formatting and lures referring to shared files or voicemails to prompt recipients to click embedded links. The attack chain used a multi-stage redirection: links hosted on storage.cloud.google[.]com redirected to googleusercontent[.]com, where users saw a fake CAPTCHA or image-based verification to block automated scanners, then landed on a counterfeit Microsoft login page hosted on a non-Microsoft domain to harvest credentials.
Key Topics
Tech, Google Cloud, Application Integration, Check Point, Oauth, Azure Ad
